ABSTRACT
The Bluetooth wireless technology
was created to solve a simple problem: replace the cables used on mobile
devices with radio frequency waves. The technology encompasses a simple
low-cost, low-power, global radio system for integration into mobile devices.
Such devices can form a quick ad-hoc secure "piconet" and communicate
among the connected devices. This technology creates many useful mobile usage
models because the connections can occur while mobile devices are being carried
in pockets and briefcases
Bluetooth uses radio waves in 2.4GHz
band. The main disadvantage of infrared communication i.e. requirement of ‘line
of sight’, gets eliminated as radio waves are used for communication in
Bluetooth. Bluetooth only operates at weak wattage levels. Bluetooth works in
small confined area of 10 to 15 meters and it can also be increased upto 100
meters by increasing power. Bluetooth use a technology called spread spectrum
frequency hopping. It gives security to the system in terms of interference
problem. Bluetooth supports not only point-to-point connections but also
multipoint connections. The multipoint connection of devices is called as
piconet and network of many piconets form scatternet. Piconet is also called as PAN i.e. ‘Personal
Area Network’.In this paper ww will discuss brief about working
Chipsets are very small in size and
further smaller chips are in development, hence now a days Bluetooth technology
has moved fast in terms of adoptation. So the ‘Special Interest Group’ of
Bluetooth (SIG) introduced by Ericsson in 1994, has now tripled in size and has
over 2000 companies on board.
v HISTORY
The name
Bluetooth refers to the Danish king Harald Blåtand (Bluetooth) who unified Denmark Norway
The logo for Bluetooth is based
on Runes surrounding the legend of
Harald Bluetooth Bluetooth the technology is based on communications central to
man’s own personal space. Fundamentally Bluetooth operates within the
Industrial, Scientific and Medical (ISM) band at 2.4 GHz. It
is a short-range wireless
communication standard defined as cable replacement for a Personal Area Network (PAN).
v Introduction
ð what is bluetooth?
"Think of a connected
world of electronic devices and appliances around you! You click on an
icon for a device and you are linked to it, automatically and
transparently" .
The operating band also fits
the goals of Bluetooth, imposing requirements as a cable replacement. The cost needs to be comparable with cable. Reductions can be achieved by operating in the licence
free 2.4 GHz ISM band,
keeping backward compatibility wherever possible
lowers the cost of ownership by avoiding upgrades and
having a relaxed radio specification enables single chip integrated circuit
solutions. It also needs to be as reliable and resilient as cable and cope with errors and
degradation caused by interference. For mobile devices it must be compact,
lightweight, low power and easy to use.
Briefly,
Bluetooth technology
Ø Evolved
from basic cellular digital radio designs implemented in mobile phones since
the early 1980s.
ü Based
on 802.11 in ad-hoc mode
Ø Short
range (up to 10m) radio communications standard
Ø
Runs at 2.4 GHz, near microwave frequency Unlicensed part of spectrum
Ø No line of sight is required
Ø Performs
fast frequency hopping (1600 hops/sec) between 79 points to avoid interference
Ø Is
full duplex
Ø Low
power, 30-100mA during sustained data transmissions
Ø Devices
automatically switch to power saving mode
Ø Bandwidth
is wide enough to carry voice & data
ü an
asynchronous data channel, or
ü up
to 3 simultaneous synchronous voice channels, or
ü a
channel which simultaneously supports asynchronous data and synchronous voice.
Ø Transfers
data at 721 Kbps
Ø three
to eight times the average speed of parallel and serial ports, respectively.
Ø Up
to 7 simultaneous connections can be established and maintained
v Frequency Hopping
technique
We have
addressed the reasons for the Bluetooth without delving into the ‘nuts and
bolts’ of the technology to discover how it operates. For the majority of
countries the ISM band used by Bluetooth is available from 2.40-2.4835 GHz,
although some countries impose restrictions. In this band Bluetooth uses
Frequency Hopping Spread Spectrum (FHSS) techniques in order to improve its
immunity from interference.
In unrestricted countries the radios hop in pseudo
random sequences around all available channels, this equates to 79 RF
channels with a channel spacing of 1 MHz. Starting at a base frequency of 2402
MHz then the frequency of the channels, f, can be expressed as:
f =2402 + n MHz
where, n, is the channel
number with an integer value in the range of 0 to 78. In restricted countries a
limited frequency hopping schemes with just 23 channels is used and is catered
for in the Bluetooth specification. Both hopping schemes have a 1 MHz channel spacing making it possible to
design a simple radio interface whereby the baseband only has to specify a
channel number and the radio multiplies this up to the appropriate frequency
offset.
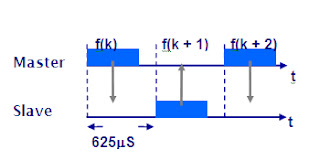
In this FHSS scheme there are 1600 hops per
second, which is a hop every 625 µs. Part of this hop timing is taken up by the
guard time of 220 µs allowing the synthesizer time to settle. The frequency
hopping implements time division multiplexing as shown in Figure 2. The basis
of the scheme has the Master device transmitting in the first 625 us slot, k,
and here the Slave receives. In the next slot k = 1 the Slave is permitted to
transmit and the master listens.
Fig: Frequency hopping,master and slave interact of corresponding slots
The radio must be able to retune and stabilise on
a new frequency within tight time constraints. This is pushed further when
establishing a connection; the hop rate can be shortened to every 312.5 us. As
the radios are constantly hopping to different radio channels, this ensures
that packets affected by interference on one channel can be retransmitted on a
different frequency channel. To further enhance resilience both ARQ (Automatic
Repeat reQuest) and FEC (Forward Error Correction) form part of the
specification.
One drawback with the normal hop
sequence is the time taken for production testing. Bluetooth ensures adequate
frequency coverage with a test sequence allowing the radios to be tested at a
faster rate
v The Protocol Stack
The Bluetooth
specifications define not only a radio system but cover the underlying
structure. The Core Specification contains a software protocol stack similar to
the more familiar Open Systems Interconnect (OSI) standard reference model for
communication protocol stacks. It permits applications to discover devices, the
services they offer and permission to use these services. The stack is a
sequence of layers with features crossing single or multiple layered
boundaries. Figure 4 outlines the stack with each block corresponding to a Core
Specification chapter. Other remaining chapters relate to compliance
requirements, test modes and test control interface.
fig : The Bluetooth protocol stack
If we
ascend the stack, we first come across the fundamental component, the radio.
The radio modulates and demodulates data for transmitting and receiving over
the air. The operating band of the radio is divided into 1 MHz spaced channels
with a chosen modulation scheme of Gaussian Frequency Shift Keying (GFSK). Each
channel is specified to signal at 1mega symbols per second, equivalent to 1
Mb/s. Above the radio are the Baseband and Link Controller, they are
responsible for controlling the physical links via the radio, assembling the
packets and controlling the frequency hopping.
Progressing
through the layers, the Link Manager (LM) controls and configures links to
other devices. The Host Controller Interface (HCI) is above the LM layer and is probably one of the
most important layers to consider as a designer. It handles communication
between host and the module. The standard defines the HCI command packets that
the host uses to control the module, the event packets used by the host to
inform lower protocol layers of changes, the data packets for voice and data traffic
between host and module and the transport layer used by the HCI packets. The
transport layer can be USB (H2), RS232 (H3), UART (4) or a robust proprietary
standard such as BCSP (BlueCore Serial Protocol).
The
Logical Link Control and Adaptation (L2CAP) is a multiplexor, adapting data
from higher layers and converting between different packet sizes. The next 4
layers could be loosely grouped as communication interfaces. These are RFCOMM
(Radio Frequency COMMunication port) which provides an RS232 like serial
interface. Wireless Application Protocol (WAP) and OBject EXchange (OBEX) are responsible for providing
interfaces to other Communications Protocols. The final member of this rough
grouping is the Telephony Control protocol Specification (TCS) providing
telephony services. Service Discovery Protocol (SDP) lets devices discover the
services available on another Bluetooth device.
The
application layer is probably obvious, but the standard provides Profiles
laying out rules for how applications use the protocol stack, ensuring
interoperability at application level.
v The Profiles—A Hierarchy of
Groups
The Bluetooth
specification defines a wide range of profiles, describing many different types
of tasks, some of which have not yet been implemented by any device or system..
For information on other profiles, including those still in development, see
the Bluetooth specification.
At a minimum, each
profile specification contains information on the following topics:
Dependencies on other profiles.
Every profile depends on the base profile, called the generic access profile,
and some also depend on intermediate profiles.Suggested user interface formats. Each profile describes how a user should view the profile
so that a consistent user experience is maintained. Specific parts of the Bluetooth protocol stack used by the profile.
To perform its task, each profile uses particular options and parameters at
each layer of the stack. This may include an outline of the required service
record, if appropriate
ð The Base Profile
At the base of
the profile hierarchy is the generic access profile (GAP), which defines a
consistent means to establish a baseband link between Bluetooth devices. In
addition to this, the GAP defines:
ü Which
features must be implemented in all Bluetooth devices
ü Generic
procedures for discovering and linking to devices
ü Basic
user-interface terminology
All other profiles are based on the GAP. This allows each profile
to take advantage of the features the GAP provides and ensures a high degree of
interoperability between applications and devices. It also makes it easier for
developers to define new profiles by leveraging existing definitions
ð Other Profiles
The
service discovery application profile describes how an application
should use the SDP (described in “The Bluetooth Protocol Stack”) to discover services
on a remote device. As required by the GAP, any Bluetooth device should be able
to connect to any other Bluetooth device. Based on this, the service discovery
application profile requires that any application be able to find out what
services are available on any Bluetooth device it connects to.
The human interface device (HID)
profile describes how to communicate with a HID class device using a
Bluetooth link. It describes how to use the USB HID protocol to discover a HID
class device’s feature set and how a Bluetooth device can support HID services
using the L2CAP layer.
As its name suggests,
the serial port profile defines RS-232 serial-cable emulation for
Bluetooth devices. As such, the profile allows legacy applications to use
Bluetooth as if it were a serial-port link, without requiring any modification.
The serial port profile uses the RFCOMM protocol to provide the serial-port
emulation.
The dial-up
networking (DUN) profile is built on the serial port profile and describes
how a data-terminal device, such as a laptop computer, can use a gateway
device, such as a mobile phone or a modem, to access a telephone-based network.
Like other profiles built on top of the serial port profile, the virtual serial
link created by the lower layers of the Bluetooth protocol stack is transparent
to applications using the DUN profile. Thus, the modem driver on the
data-terminal device is unaware that it is communicating over Bluetooth. The
application on the data-terminal device is similarly unaware that it is not
connected to the gateway device by a cable.
The headset profile describes how a
Bluetooth-enabled headset should communicate with a computer or other Bluetooth
device (such as a mobile phone). When connected and configured, the headset can
act as the remote device’s audio input and output interface.
The hardcopy
cable replacement profile describes how to send rendered data over a
Bluetooth link to a device, such as a printer. Although other profiles can be
used for printing, the HCRP is specially designed to support hardcopy
applications.
The generic
object exchange profile provides a generic blueprint for other profiles
using the OBEX protocol and defines the client and server roles for devices. As
with all OBEX transactions, the generic object exchange profile stipulates that
the client initiate all transactions. The profile does not, however, describe
how applications should define the objects to exchange or exactly how the applications
should implement the exchange. These details are left to the profiles that
depend on the generic object exchange profile, namely the object push, file
transfer, and synchronization profiles.
The object
push profile defines the roles of push server and push client. These roles
are analogous to and must interoperate with the server and client device roles
the generic object exchange profile defines. The object push profile focuses on
a narrow range of object formats for maximum interoperability. The most common
of the acceptable formats is the vCard format. If an application needs to
exchange data in other formats, it should use another profile, such as the file
transfer profile.
The file
transfer profile is also dependent on the generic object exchange profile.
It provides guidelines for applications that need to exchange objects such as
files and folders, instead of the more limited objects supported by the object
push profile. The file transfer profile also defines client and server device
roles and describes the range of their responsibilities in various scenarios.
For example, if a client wishes to browse the available objects on the server,
it is required to support the ability to pull from the server a folder-listing
object. Likewise, the server is required to respond to this request by
providing the folder-listing object.
The synchronization
profile is another dependent of the generic object exchange profile. It
describes how applications can perform data synchronization, such as between a
personal data assistant (PDA) and a computer. Not surprisingly, the
synchronization profile, too, defines client and server device roles. The
synchronization profile focuses on the exchange of personal information
management (PIM) data, such as a to-do list, between Bluetooth-enabled devices.
A typical usage of this profile would be an application that synchronizes your
computer’s and your PDA’s versions of your PIM data. The profile also describes
how an application can support the automatic synchronization of data—in other
words, synchronization that occurs when devices discover each other, rather
than at a user’s command.
v
Piconet,and Scatternet
ð Master and Slave Operation.
Bluetooth
devices exist in small ad-hoc network configuration with the ability to operate
as either master or the slave; the specification also allows a mechanism for
master and slave to switch their roles. The configurations can be single point,
which is the simplest configuration with one master and one slave. Multipoint,
called a Piconet, based on up to 7
slaves clustered around a single Master. And a third type called a Scatternet, this is a group of Piconets
effectively hubbed via a single Bluetooth device acting as a master in one
Piconet and a slave in the other Piconet. The Scatternet permits either larger
coverage areas or number of devices than a single Piconet can offer. Figure 5
outlines the different master and slave topologies permitted for networks in
the standard.
fig : point to point ,piconet
& scatternet
The
role of the master is to control the available bandwidth between the slaves, it
calculates and allocates how often to communicate with each slave and locks
them into the appropriate frequency hopping sequence. The specification
describes an algorithm that calculates the hop sequence, the seed being based
on the master’s device address and clock. In addition to hop sequence control,
the master is responsible for transmit control by dividing the network into a
series of time slots amongst the net members, as part of a Time Division
Multiplexing (TDM) scheme. These time slots can consist of data and potentially
additional voice traffic i.e. you will always need a data channel before you
can add a voice channel. The time slot is defined as 625 µs and all packet
traffic is allocated 1, 3 or 5 slots, grouped together in transmit and receive
pairs. Prior to connection some operations such as inquiry, paging and scanning
operations may sometimes occur on half slots.
v bluetooth Security
Ø Bluetooth
guarantees security at the bit level. Authentication of any device is
controlled by the user by using a 128 bit key. Radio signals can be coded with
8 bits or anything up to 128 bits.
Ø Bluetooth protocol has these
components:
ü
Random Number Generation
ü
Encryption (128-bit WEP)
ü
Encryption Key Management
ü
Authentication
Ø Devices can be assigned a PIN which
must be verified before others can access it
Ø Devices have unique 48 bit Bluetooth
address
Ø Bluetooth
uses Frequency Hopping Spread Spectrum (FHSS) techniques in order to improve
its immunity from interference. .
Ø Fast frequency hopping provides some
security
ü Only
synchronised nodes can follow transmissions
Ø Uses
checksums & FEC (Forward Error Correction) to detect & fix corruption
of data & limits the impact of random noise on long-distance links.
v comparison with infrared and 802.11b
ð Infrared
vs. Bluetooth
Ø The
infrared beams have a major disadvantage because it is all done by line of
sight.
Ø Line
of sight is exactly how your eyes function; if you can not see an object you do
not know it’s there.
Ø The
infrared transmitter must be in direct sight of the device.
Ø This
means the user can not use the device in other rooms and it has a weaker signal
since it always has to be in direct sight of the transmitter.
Ø Since Bluetooth uses radio signals, the
devices do not have to be in direct sight of the Bluetooth transmitter
ð BLUETOOTH AND 802.B
Bluetooth's biggest perception problem has nothing to do with Bluetooth
itself. The meteoric rise in popularity of IEEE 802.11b (WiFi) wireless
networking devices has left many users wondering if they need Bluetooth at all.
IEEE 802.11b offers faster speeds and greater range than Bluetooth. To further
confuse matters, the two systems share space in the unlicensed 2.4 GHz radio
spectrum, and it is possible for Bluetooth and IEEE 802.11b systems to
interfere with one another.
There's also a public
perception that IEEE 802.11b and Bluetooth compete with one another. While both
can be used to connect computers into an ad-hoc network, the two systems are
really complementary technologies that meet very different needs. Refer to the
table below for important fundamental differences between Bluetooth and IEEE
802.11b.
|
Contrasting Technologies
|
||
|
|
||
|
|
Bluetooth
|
IEEE 802.11b
|
|
Access
|
Doesn't typically have an access point--devices on a
Bluetooth PAN communicate directly with one another.
|
IEEE 802.11b allows mobility over a very large area. When
out of range of one IEEE 802.11b access point, another takes over.
|
|
Use of Radio Band/Spectrum
|
2.4 GHz radio band/Frequency Hopping Spread Spectrum
(FHSS)
|
2.4 GHz radio band/Direct Sequence Spread Spectrum (DSS)
|
|
QOS Features
|
Yes
|
A proposed extension will add this feature, paving the way
for wireless IP telephones
|
|
Radio Signal
|
Weaker signal provides for more conservative use of
battery power (designed for PDAs, wearable headsets, cell phones)
|
Stronger signal provides more power but uses 10 to 100
more power than Bluetooth (designed for notebook computers, where the
additional current drain is negligible
|
v Advantages &
Disadvantages
ü Advantages
1.
It eliminates the need of cables or wires for
connecting various devices.
2.
The
capital cost is low .
3.
Chips are available in very small size having area 0.9
cm square, and much smaller chip versions are in development.
4.
Almost any
electronic device can be connected.
5.
Unlike infra-red, Bluetooth does not require
line-of-sight positioning of connected devices.
ü Disadvantages
1.
The maximum range
for this technology is 10 meter, which limits the space of PAN and/or limits
the connection accessibility needed by other electronic devices to perform an
action.
2.
The maximum
capacity of data transmission with this technology one mega bit per second,
which makes the information exchange very slow when handling large size files
or folders.
v Applications
Automatic
communication between various devices within a small area makes it possible to
provide unique and innovative services to the professional workers using portable devices. Bluetooth
technology has this potential and is coming along fast and quick. It will
replace clumsy wires, make information transfer automatic and introduce many
new applications, as follows
1.
The Bluetooth technology connects all office
peripherals wirelessly. We can connect
PC or notebook to printers, scanners and faxes without cable
attachments.
2.
If digital camera is
Bluetooth enabled, we can send
video images from any location to any location without the hassle of
connecting the camera to the mobile phone on the wire line phone.
3.
Bluetooth allows us to have three way
phones. At home, your phone functions as a portable phone (fixed line charge).
When you're on the move, it functions as a mobile phone (cellular charge). And
when your phone comes within range of another mobile phone with built-in
Bluetooth wireless technology it functions as a walkie-talkie (no telephony
charge).
4.
We can connect
wireless headset to mobile phone, mobile computer or any wired connection to keep our hands free for
more important tasks when we're at the
office or in car.
5.
Automatic Message
Delivery : Compose e-mails on portable
PC while you're on an airplane. As soon as you've landed and switched on your
mobile phone, all messages are immediately sent.
6.
Upon arriving at the home, the door automatically
unlocks, the entry way lights come on, and the heat is adjusted to pre-set
preferences.
7. There
are in automobile’s navigation system, when the driver opens the car door with
his or her palm pilot, the palm and navigation system automatically communicate
and transfer driving instructions.
v
Conclusion
This was an
overview of Bluetooth giving insight to the key features and potential
challenges of the technology. The technology occupies the 2.4 GHz ISM band
sharing the bandwidth with potential competing standards. It defines a Personal
Area Network (PAN) whereas others advocate a Wide Area Network (WAN) approach.
It is best positioned as a short-range wireless standard designed with the same
cost goals and similar or greater reliability and performance as the cable it
replaces. Based on a frequency agile FHSS scheme it leverages hopping to avoid
interference and it was not intended as a replacement for wireless LAN in a WAN
scenario, because as yet it does not fully specify a hand over mechanism.
The importance
of the Bluetooth SIG and how its specifications aid development of applications
was highlighted, especially through the profiles, and their interoperability is
assured through the qualification process. A flavour of the applications was
explored through the functionality and where particular attention must be paid
to the protocol stack for system segmentation. But to thoroughly investigate
Bluetooth a list of further reading and applicable websites is given in the
reference section. The latest specifications including the profiles are
available from the Bluetooth SIG website. Reading specifications can seem a
little ‘one dimensional’ but read in conjunction with a good book, whilst using
a development tool from one of the Bluetooth silicon vendors, then the jigsaw
pieces to really start to fit.
Still, with its all advantages, the Bluetooth technology is in its
primary stages. Hence, we hope that, through the impending development phases,
it will have the potential to address most of its current shortcomings.
v rererences
ð J. Bray and C.F. Sturman, “Bluetooth: Connect
Without Cables”, Prentice Hall.





No comments:
Post a Comment